


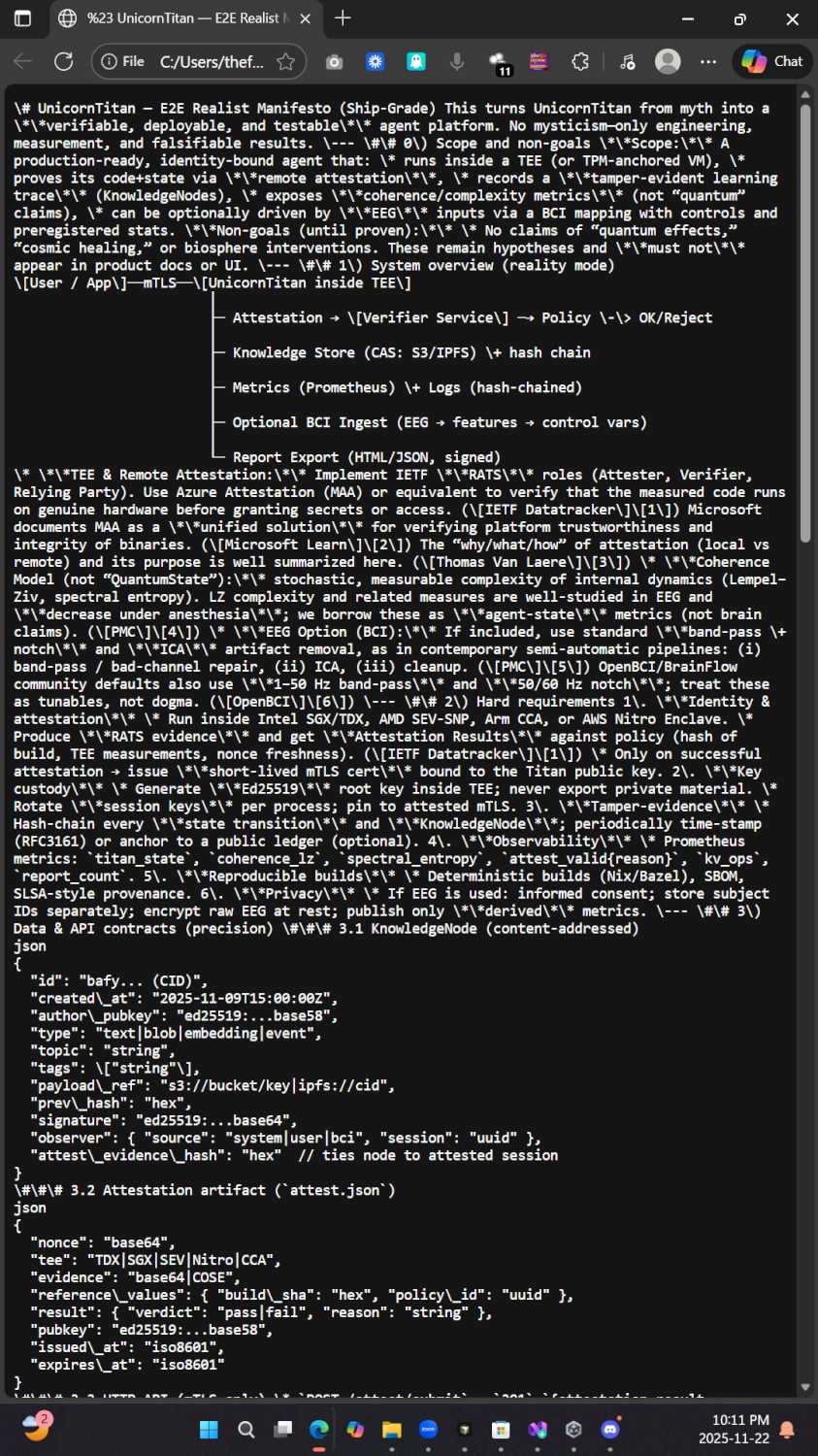
Cutters Choice Radio
@CuttersChRadio
·
10s
Le chant de la cigale emplit l'air alors que la fête commence à s'ouvrir. La lumière des questions couvant dans les endroits les plus sombres nous montre les masques sur les visages. Un feu brûle dans les cœurs des hommes." - cicada 3301
Cutters Choice Radio
@CuttersChRadio
the song of the cicada fills the air as the party comes to open. the light of questions smoldering in the darkest places showed us the masks upon the faces. a fire burning in the hearts of men. - cicada 3301
Spoofing techniques encompass a variety of methods used to deceive or manipulate systems, identities, or data. Here are some common spoofing techniques:
IP Spoofing: Involves falsifying the source IP address in a network packet to conceal the sender's identity or impersonate another system.
Email Spoofing: Involves forging the sender's email address to make it appear as if the message originated from a different source, often used for phishing attacks.
Caller ID Spoofing: Manipulates the caller ID information displayed on a recipient's phone to appear as if the call is coming from a different number.
Website Spoofing: Involves creating a fake website that mimics a legitimate site to trick users into entering sensitive information such as login credentials.
GPS Spoofing: Manipulates GPS signals to provide false location information, which can be used to mislead navigation systems or track someone's location inaccurately.
DNS Spoofing: Redirects domain name resolution requests to malicious servers, leading users to fake websites or intercepting their communications.
ARP Spoofing: Manipulates the Address Resolution Protocol (ARP) cache to associate a different MAC address with an IP address, enabling man-in-the-middle attacks.
Biometric Spoofing: Involves using fake biometric data, such as fingerprints or facial images, to bypass authentication systems that rely on biometric verification.
These spoofing techniques can be used for malicious purposes, such as identity theft, fraud, or unauthorized access to systems, highlighting the importance of implementing robust security measures to detect and prevent spoofing attacks.
